S-360 as SP
S-360 can serve as an Service Provider (SP) using OpenIDConnect (OIDC) protocol.
Table of Contents
- 1. Introduction
- 2. Linking between external identifier and Secutix contact
- 3. Configuration
- Technical limitations
- Annexe 1 : example of Cognito documentation
- Annexe 2 : example of setup with addresses and phone number transmissions
- Annexe 3 : example of setup with titles, criteria and authorizations
1. Introduction
Use any third-party web app that implements the server side of the OpenID Connect protocol, such as Keycloak, Amazon and Paypal as an authentication provider. The goal is to allow a final user to go to ticketshop and avoid him to enter credentials : he will be able to connect automatically to ticketshop through an external Identity Provider. Here is the example of OurClient which is using Keycloak solution to have a SSO (Single Sign On) in many websites.
When a user comes to OurClient website, he will be redirected* to the external Identity provider and will follow some steps before coming back to ticketshop with his account:
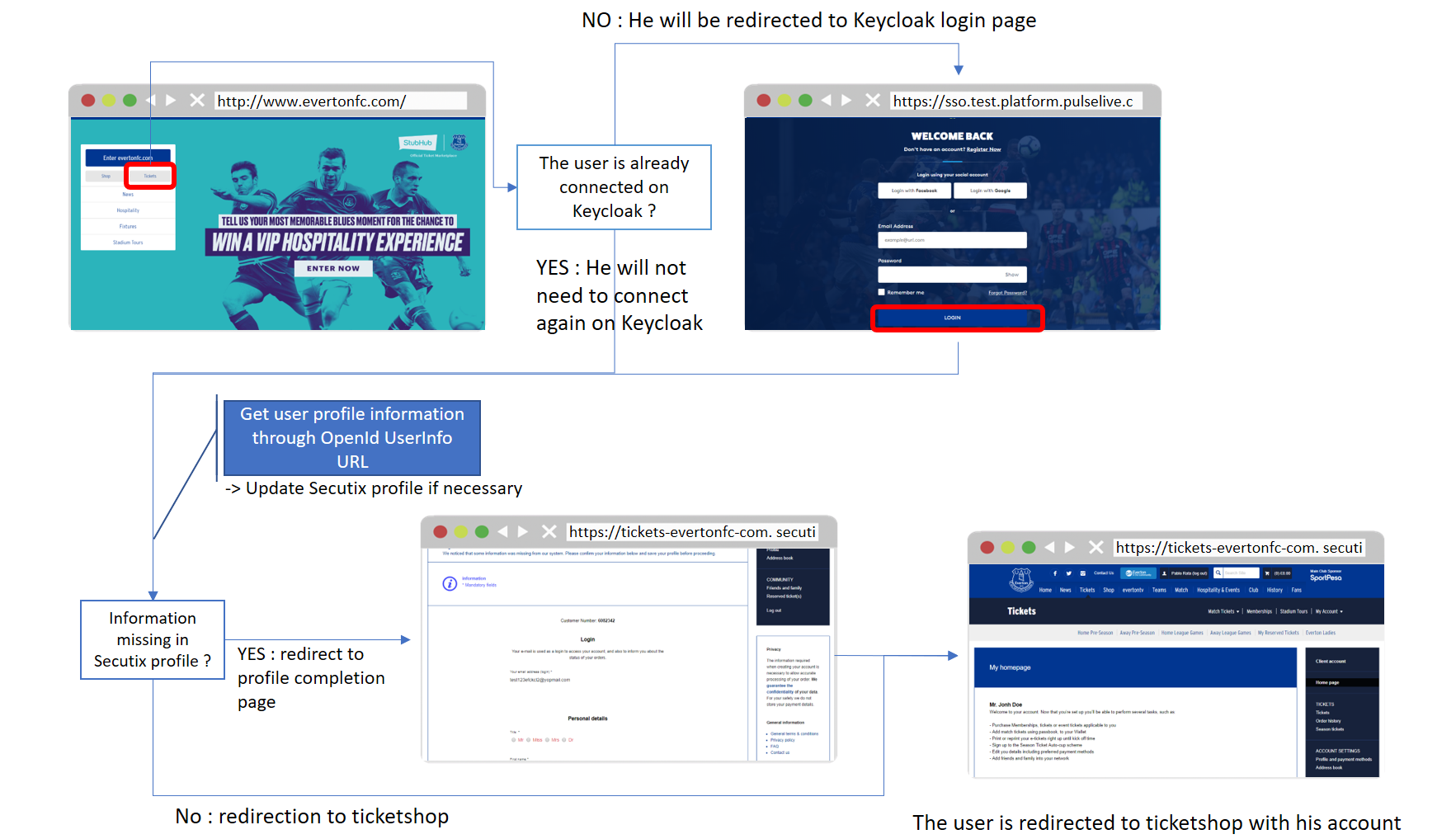
(* Side note : in that case, the user is directly redirected to the SSO page because the connection mode is "Exclusive". Check the chapter "Configuration" just below for more details about exclusive mode)
2. Linking between external identifier and Secutix contact
Here is how Secutix Ticketshop will handle the linking to the Secutix contact during connection:
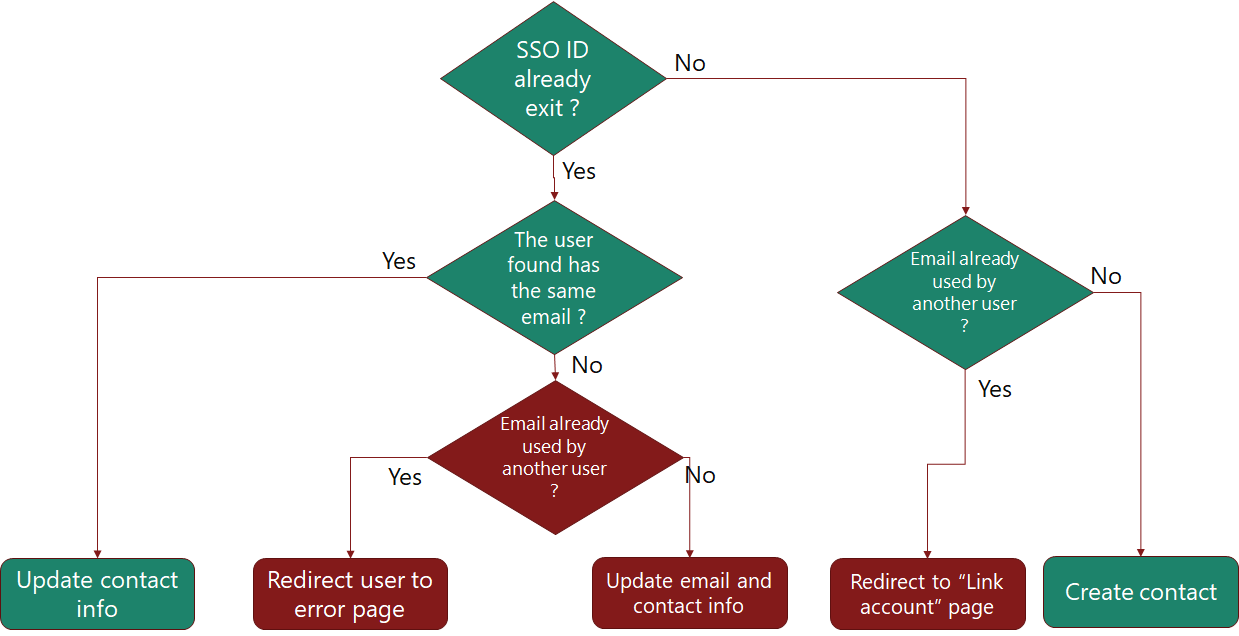
The path in green in the normal path that will be followed by the system if the migration and the integration with the external system worked correctly.
The red cases should not happened. For example, having the SSO ID already used by a contact that has a different email is a case that should not happened.
For the the case where the user is redirected to "Link account" page, this is a very critical part because the user will be asked to provide the Secutix password of the contact that has the same email address. In case of exlusive SSO (it is only possible to connect to ticketshop with the SSO), this account might not have any password (in case the account was created through SSO) and the user then will not be able to merge the accounts and neither to connect to ticketshop.
Here is the power point file that contains the diagram (this file contains also the behavior for Lottery part).
3. Configuration
To configure a new OpenId Connect authentication provider:
-
Go to Sales Channels > Points of sale > Social network:
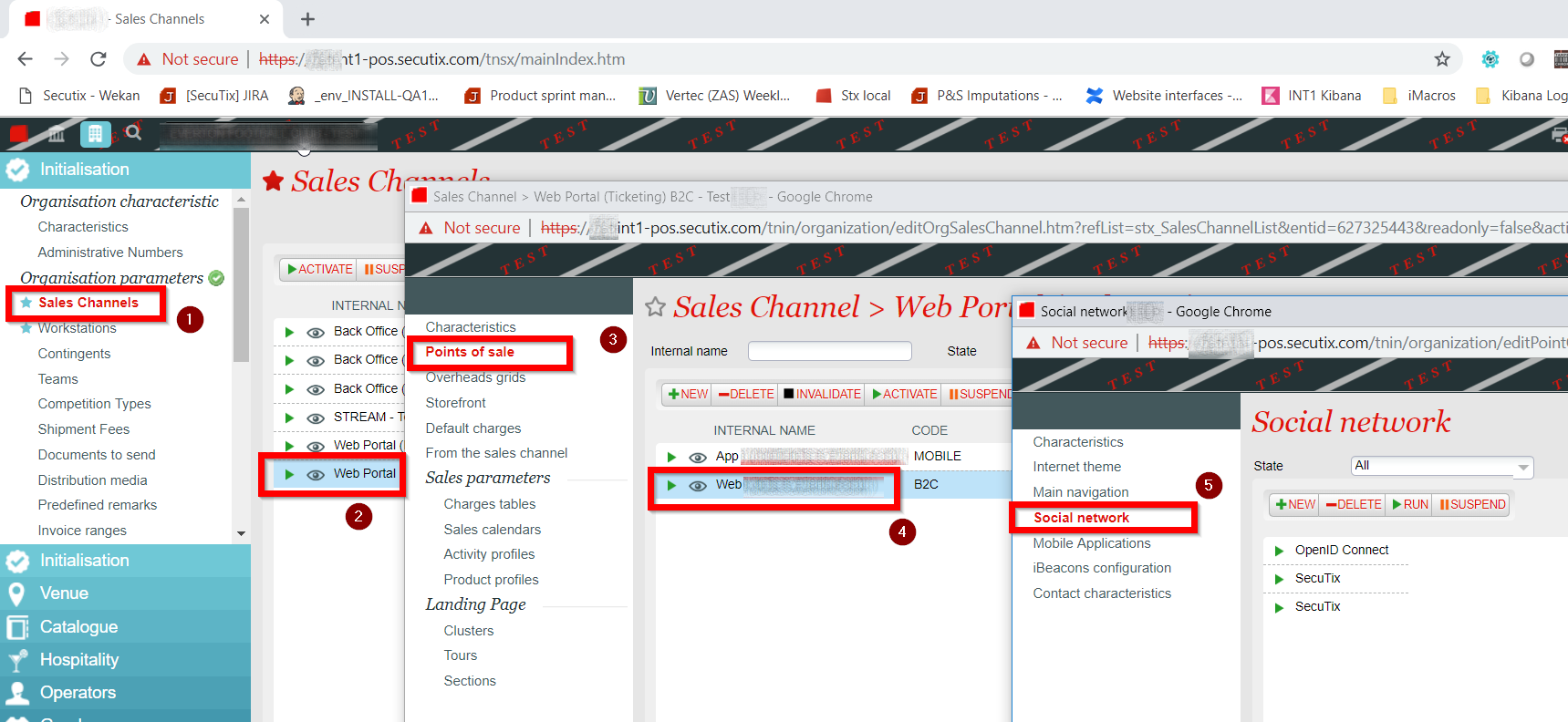
Here is an example of configuration that we used for Keycloak for OurClient :
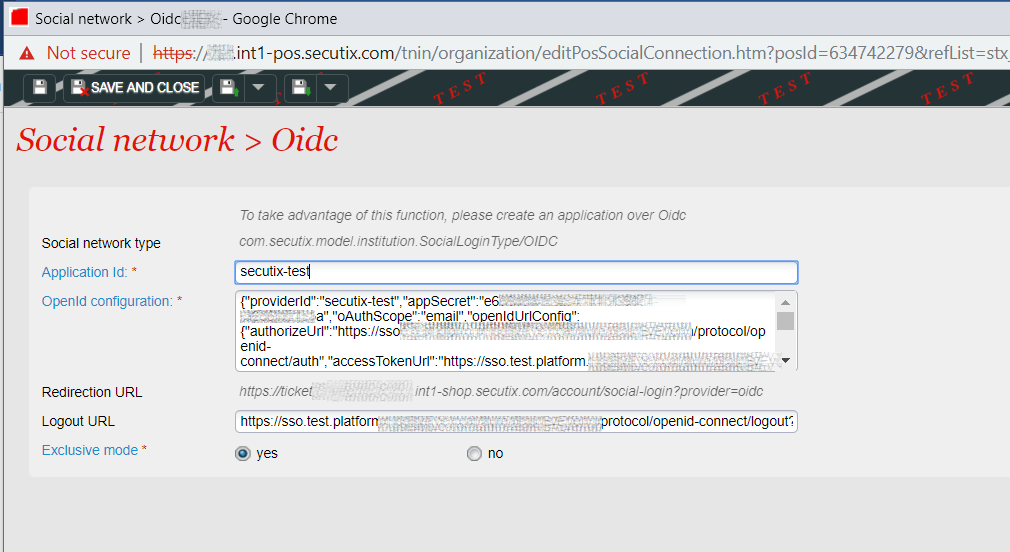
-
Application Id → client id
-
OpenId Configuration → JSON configuration in the following format:
{ "providerId": "secutix-test", "appSecret": "e6*********************5a", "oAuthScope": "email", "openIdUrlConfig": { "authorizeUrl": "https://sso.test.platform.*****integrator.com/auth/realms/OurClient/protocol/openid-connect/auth", "accessTokenUrl": "https://sso.test.platform.*****integrator.com/auth/realms/OurClient/protocol/openid-connect/token", "authenticateUserUrlAdditionalParam": "", "userInfoUrl": "https://sso.test.platform.*****integrator.com/auth/realms/OurClient/protocol/openid-connect/userinfo" }, "defaultPhoneNumberCountryCode":"GB", // OPTIONAL "setAddressAsShippingAddress": true, // OPTIONAL "openIdProfilePath": { "userIdProfilePath": "sub", "emailProfilePath": "email", "firstNameProfilePath": "given_name", "lastNameProfilePath": "family_name", "genderProfilePath": "" } } -
Those values are standard OpenId Connect parameters. The values that are specific to Secutix are:
- openIdUrlConfig.authenticateUserUrlAdditionalParam : parameters that can be added to the authorize URL when authenticating the user.
Example : "&access_type=online" - openIdProfilePath : contains the keys that will be used to get the contact infos from the response of the call to UserInfo Rest API (OIDC standard).
- defaultPhoneNumberCountryCode : OPTIONAL. If set, the prefix for phone numbers will be calculated based on the country code (in capitals). Example: "GB". By default: "CH"
- setAddressAsShippingAddress: OPTIONAL. If set to true, the address coming from the IDP will be set as shipping address.
- setAddressAsBillingAddress: OPTIONAL. If set to true, the address coming from the IDP will be set as billing address.
For example, this configuration was done for this type of response:
{ "sub": "4355beb8-82a9-4245-ac21-6b5ccd60e3df", "email_verified": true, "name": "John Doe", "preferred_username": "johndoe@yopmail.com", "given_name": "John", "family_name": "Doe", "email": "johndoe@yopmail.com" } - openIdUrlConfig.authenticateUserUrlAdditionalParam : parameters that can be added to the authorize URL when authenticating the user.
Technical limitations
Grant types
S-360 OIDC connector only supports Authorization code grant type. Token and id_token are not supported.
Annexe 1 : example of Cognito documentation
{
"providerId": "cognito",
"appSecret": "b4f******db",
"oAuthScope": "email",
"openIdUrlConfig": {
"authorizeUrl": "https://secutix-test-mosa.auth.eu-west-1.amazoncognito.com/oauth2/authorize",
"accessTokenUrl": "https://secutix-test-mosa.auth.eu-west-1.amazoncognito.com/oauth2/token",
"authenticateUserUrlAdditionalParam": "",
"userInfoUrl": "https://secutix-test-mosa.auth.eu-west-1.amazoncognito.com/oauth2/userInfo"
},
"openIdProfilePath": {
"userIdProfilePath": "sub",
"emailProfilePath": "email",
"firstNameProfilePath": "given_name",
"lastNameProfilePath": "family_name",
"genderProfilePath": ""
}
}Annexe 2 : example of setup with addresses and phone number transmissions
{
"providerId":"secutix-test",
"appSecret":"e6*************************4c15a",
"oAuthScope":"email",
"openIdUrlConfig":{
"authorizeUrl":"https://sso.test.platform.xxxxxxxlive.com/auth/realms/OurClient/protocol/openid-connect/auth",
"accessTokenUrl":"https://sso.test.platform.xxxxxxxlive.com/auth/realms/OurClient/protocol/openid-connect/token",
"authenticateUserUrlAdditionalParam":"",
"userInfoUrl":"https://sso.test.platform.xxxxxxxlive.com/auth/realms/OurClient/protocol/openid-connect/userinfo"
},
"defaultPhoneNumberCountryCode":"GB",
"openIdProfilePath":{
"userIdProfilePath":"sub",
"emailProfilePath":"email",
"firstNameProfilePath":"given_name",
"lastNameProfilePath":"family_name",
"genderProfilePath":"",
"addressLine1Path":"addressline1",
"addressLine2Path":"addressline2",
"addressLine3Path":"",
"postalCodePath":"postcode",
"countryCodePath":"country",
"addressTownPath":"city",
"phoneNumberPath":"mobile",
"dateOfBirthPath":"dob"
}
}Annexe 3 : example of setup with titles, criteria and authorizations
{
"providerId": "******************************",
"appSecret": "*********************",
"requestLogs": true,
"createContactWithInternetAccount": false,
"oAuthScope": "email",
"openIdUrlConfig": {
"authorizeUrl": "https://sso.provider.com/services/oauth2/authorize",
"accessTokenUrl": "https://sso.provider.com/services/oauth2/token?format=json",
"authenticateUserUrlAdditionalParam": "",
"userInfoUrl": "https://sso.provider.com/services/oauth2/userinfo?format=json"
},
"defaultPhoneNumberCountryCode": "GB",
"titleMappings": {
"M": "MR",
"F": "MRS",
"default": "UNDEFINED"
},
"setAddressAsShippingAddress": true,
"openIdProfilePath": {
"userIdProfilePath": "sub",
"emailProfilePath": "email",
"firstNameProfilePath": "given_name",
"lastNameProfilePath": "family_name",
"addressLine1Path": "addressline1",
"addressLine2Path": "addressline2",
"addressLine3Path": "",
"postalCodePath": "postcode",
"countryCodePath": "country",
"addressTownPath": "city",
"phoneNumberPath": "phone_number",
"dateOfBirthPath": "dob",
"genderProfilePath": "gender",
"authorizations": {
"CNIL_O": "optin1",
"CNIL_T": "optin2"
},
"criteria": {
"NEWSLETTER": "optinNL",
"USERNAME": "preferred_username"
}
}
}